Cyber security is a stream that follows preventive methods to protect information from being stolen, compromised or attacked. This stream requires a deep understanding of potential computer threats and malicious activities. Cyber security also deals with controlling physical access to hardware which is connected to a network.
Let’s dive deep into Cyber-Security world. Any malicious activity to be performed requires an attacker to gain access to the network at first place and this is where humans come into the picture. There are numerous instances where human mistakes caused a bug which led to an attack which did not require any kind of hacking.

Perfect example for this is the software vulnerabilities in the Bank of Maharashtra’s Unified Payment Interface app which was recently exploited to complete digital transactions even when there was insufficient balance in the sender’s account. The small human mistake in API (Application Programming Interface) development message cost a huge scam of Rs. 25 crores. No hacking required!!
Another example is the most recent ransomware attacks. This attack broke the system into pieces and currently estimated to have locked up more than a lakh computers across hundred countries. A tool created by NSA (National Security Agency, USA) for tracking terrorist activities somehow fell in wrong hands and cost this lockdown.

Designing Cyber security for any institution is a complex job. Small loop holes may lead to catastrophic outcomes or shatter the economy or may cost lives.
Let’s talk about you, do you use ‘Virtual keyboard’ while logging into your bank account? No!! Right? It is not only you who is reluctant to use Virtual Keyboards, 99% of users might not be using the feature. The main reason for this is the design of the virtual keyboard.
The password we set is generally the combination of alphanumerical characters and virtual keyboards are not really designed by taking this into consideration. Below are two examples of Design centric virtual keyboard and Non-Design centric virtual keyboard.
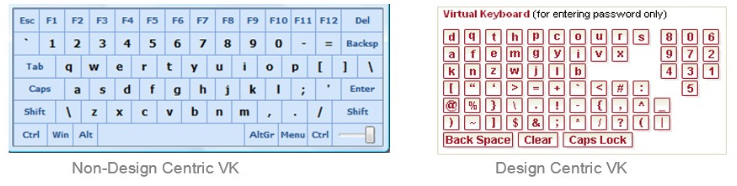
So? What would you prefer? Design Centric or another one? I leave it to you.
Another thing I find common in people is that they have no idea about choosing a secure password. Since a decade we either rely on Password Generators or we simply add alphanumerical characters anywhere in the string.
For example,
- What I want to set – typewriter
- What Gmail expects me to set – $_G@@g1e_$
- What I eventually set (after frustration) – typewriterA1@$
Is this a secure password? Let’s hear it from Bruce Schneier(Bruce Schneier is an American cryptographer) –
A typical password consists of a root plus an appendage. The root isn’t necessarily a dictionary word, but it’s usually something pronounceable. An appendage is either a suffix (90% of the time) or a prefix (10% of the time).
One cracking program I saw started with a dictionary of about 1,000 common passwords, things like “letmein,” “temp,” “123456,” and so on. Then it tested them each with about 100 common suffix appendages: “1,” “4u,” “69,” “abc,” “!,” and so on. It recovered about a quarter of all passwords with just these 100,000 combinations.
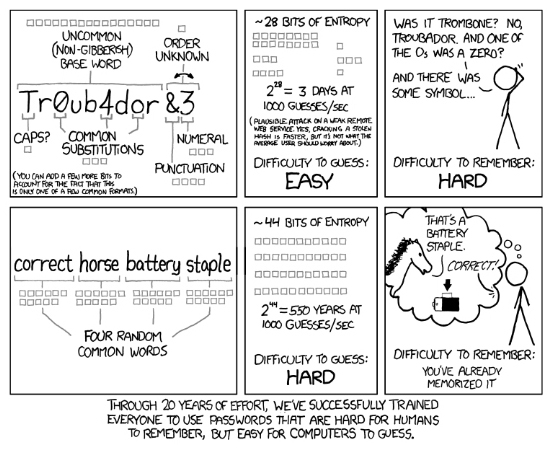
Above image shows ways to select passwords in the plain text format and it would take years for crackers to crack them. But not everyone is aware of this technique and not everyone will follow the same approach. So better way was to use alphanumeric keywords. Bottom line, no password is secure until and unless you make a mistake like saving it in notes or adding personal details like name, address or birthdate to it.
Although a technique to make your password stronger-
Take a sentence and turn it into a password. For example,
Sentence – I went home after 10 years to see my 95 years old grandma in 1997.
Password – IwH@10ytsm95yogi1997
Sentence – India is a developing nation and will be super-power in 2020 as said by Dr. Kalam
Password – Iiadn&wbs-pi2020asbDr.K

Millennials today checks-in their current location each time they visit some place and google, facebook or your phone manufacturer for that matter track you all the time.
Welcome to the Virtual World. You are not safe once you connect to the NETWORK and sad part is you have to be in NETWORK.
Today’s Enterprise and their customers are not safe at all. Everyone is prone to attacks, data frauds and insecure network architectures. Every Individual or Enterprise must take care of their data and network to avoid potential threats to the system.
Bibliography
Alex Hern, (2017) ‘Ransomware attack’, The Guardian
Satyanarayana Iyer, (2017) ‘Bank of Maharashtra files FIR against 50 people in UPI fraud‘, The Time of India
Computer Security – Cybersecurity’, Wikipedia
Bruce Schneier (2014) ‘Choosing a Secure Password’, Boingboing.net
Here is an article you might be interested in. Cybersecurity may be complex, the solutions need not be
Amplify your brand presence with the best UX design studio that truly aligns your needs with those of your consumers! Get in touch with us at YUJ Designs, today!